Yes, generally, the C4/C6 diagnostic tools and related software often require administrator privileges on your host PC for proper installation and functionality. DTS-MONACO.EDU.VN provides in-depth resources to ensure a smooth setup and optimal performance. Diving into this topic, we’ll explore the reasons behind this requirement, the potential implications, and how you can effectively manage these permissions for car coding, ECU programming, and automotive diagnostics. Understanding software compatibility, system security, and access controls will help you navigate the complexities of modern automotive technology.
Contents
- 1. Why Do C4/C6 Drivers and Software Often Need Admin Rights?
- 2. What Are the Implications of Running Software with Administrator Privileges?
- 3. How to Properly Install C4/C6 Software with Admin Rights on Windows
- 4. What Are the Risks of Granting Unnecessary Admin Privileges to Software?
- 5. Can You Run C4/C6 Software Without Admin Privileges?
- 6. What Are the Alternatives to Granting Full Admin Rights?
- 7. How Does User Account Control (UAC) Impact Software Permissions?
- 8. What Steps to Take if C4/C6 Software Fails to Run Without Admin Rights?
- 9. How Can Virtualization Help Manage Software Permissions?
- 10. Best Practices for Maintaining Security While Using Diagnostic Tools
- 11. Understanding Software Compatibility and Operating Systems
- 12. How Access Controls Affect Software Usage
- 13. The Importance of Regular Software Updates and Patches
- 14. Troubleshooting Common Installation Issues
- 15. Security Audits and Compliance in Automotive Diagnostics
- 16. How to Choose Secure and Reliable Diagnostic Software
- 17. The Future of Automotive Diagnostics and Security
- 18. How to Get Support and Training for C4/C6 Software
- 19. Key Takeaways for Managing Software Permissions
- 20. Optimizing Your Workflow With DTS-MONACO.EDU.VN
- FAQ
- Does DTS-Monaco require administrator privileges during installation?
- Why does diagnostic software need administrator rights?
- Is it safe to always run software with admin privileges?
- Can I run C4/C6 software without admin rights?
1. Why Do C4/C6 Drivers and Software Often Need Admin Rights?
Yes, C4/C6 diagnostic tools and their associated software often require administrator privileges on the host PC. This is primarily because they need to make system-level changes.
The necessity for administrator rights stems from several technical demands:
-
Driver Installation: Drivers for interfaces like the C4/C6 often need to install themselves at a system level to communicate properly with the hardware. This requires elevated privileges to access and modify system files.
-
Registry Modifications: The software might need to make changes to the Windows Registry to configure itself correctly and ensure seamless operation. Altering the registry is a protected function that needs admin rights.
-
System File Access: Diagnostic tools often read and sometimes write to protected system files to gather information or to perform tasks such as flashing or reprogramming ECUs. Such file operations necessitate administrative permissions.
-
Service Installation: Certain components may run as Windows services, which require elevated privileges to install and manage.
-
Security Policies: To adhere to security protocols and to prevent unauthorized access or modifications to sensitive system settings, admin rights are mandated.
The need for these permissions is not unique to C4/C6 tools. Many professional-grade software applications require similar access to ensure they function correctly and without causing conflicts within the operating system.
2. What Are the Implications of Running Software with Administrator Privileges?
Running diagnostic software with administrator privileges has several implications that users should be aware of, balancing functionality with security:
-
Increased Functionality: Administrator rights grant the software the ability to perform necessary tasks such as driver installation, system-level modifications, and access to protected areas of the operating system. This ensures that all features of the diagnostic tool can be utilized without restriction.
-
Enhanced Security Risks: Running software with elevated privileges increases the potential impact of security breaches. If the software has vulnerabilities, malware could exploit these to gain control of the system.
-
System Stability: Improperly written software with admin rights can cause system instability by making incorrect changes to crucial system files or settings.
-
User Account Control (UAC) Prompts: Users will frequently encounter UAC prompts, which, while a security feature, can become cumbersome if they appear too often.
-
Compliance Issues: In corporate environments, requiring admin rights can conflict with security policies aimed at limiting user privileges to reduce risk.
-
Reduced User Accountability: Actions performed by the software are executed under the administrator account, making it harder to trace specific actions back to individual users.
To mitigate these risks, it’s important to ensure that the software comes from a reputable source, is regularly updated to patch vulnerabilities, and is used in a controlled environment where the potential for misuse is minimized. According to a study by the SANS Institute, limiting admin rights is one of the most effective ways to prevent malware infections.
3. How to Properly Install C4/C6 Software with Admin Rights on Windows
To properly install C4/C6 software with administrator rights on Windows, follow these steps to minimize risks and ensure correct installation:
-
Download from a Trusted Source: Always download the software from the official vendor website or a verified source like DTS-MONACO.EDU.VN to avoid malware.
-
Disable Antivirus Temporarily: Sometimes, antivirus software can interfere with the installation. Temporarily disable it, but remember to turn it back on after installation.
-
Run as Administrator:
- Locate the setup file (e.g., setup.exe or install.exe).
- Right-click the file.
- Select “Run as administrator.”
-
Follow On-Screen Instructions: Follow the installation wizard, accepting license agreements and choosing the appropriate installation directory.
-
Address UAC Prompts: User Account Control (UAC) prompts will appear. Click “Yes” to allow the software to make changes to your computer.
-
Install Drivers: If prompted, install the necessary drivers for the C4/C6 interface. Ensure that these drivers are also from a trusted source.
-
Reboot the Computer: After the installation, reboot your computer to ensure that all components are properly configured.
-
Verify Installation: Launch the software and verify that it functions correctly. Check device manager to ensure drivers are properly installed without any conflicts.
-
Re-enable Antivirus: Turn your antivirus software back on.
-
Create a Standard User Account: For daily use, consider using a standard user account to limit the potential damage from malware. Only switch to the administrator account when necessary for software updates or system changes.
By following these steps, you can install the software correctly while minimizing the security risks associated with running programs with administrator privileges.
4. What Are the Risks of Granting Unnecessary Admin Privileges to Software?
Granting unnecessary administrator privileges to software introduces significant risks that can compromise system security and data integrity:
-
Malware Exploitation: Malware can exploit elevated privileges to gain full control over the system, leading to data theft, system corruption, or use as a bot in a network.
-
Unauthorized Access: Unnecessary admin rights can allow software to access sensitive files, system settings, and other applications without proper authorization.
-
Data Breaches: Software with excessive permissions can potentially expose sensitive data to unauthorized third parties, leading to data breaches and privacy violations.
-
System Instability: Poorly designed or buggy software running with admin privileges can cause system instability, crashes, and other operational issues.
-
Circumvention of Security Measures: By operating with elevated privileges, software can bypass security measures designed to protect the system, such as User Account Control (UAC) and other permission checks.
-
Increased Attack Surface: The more software that runs with admin rights, the larger the attack surface available to potential threats, making the system more vulnerable overall.
Limiting software to the least privilege necessary is a fundamental security principle that helps minimize these risks. According to Microsoft’s security guidelines, applications should only request the permissions they absolutely need to function correctly.
5. Can You Run C4/C6 Software Without Admin Privileges?
In many cases, running C4/C6 software without administrator privileges is possible, but it often depends on the specific functions you need to perform. Here’s a breakdown:
-
Basic Diagnostic Functions: Simple diagnostic tasks such as reading fault codes or viewing basic sensor data might be possible without admin rights.
-
Limited Functionality: Features requiring system-level changes, like ECU flashing, module programming, or advanced configurations, usually need admin privileges.
-
Compatibility Mode: Running the software in compatibility mode for older versions of Windows might reduce the need for elevated privileges.
-
User Account Control (UAC): Adjusting UAC settings can allow some tasks to be performed without full admin rights, although this may reduce system security.
-
Virtual Machines: Running the software in a virtual machine can isolate it from the host system, reducing the risk of granting admin privileges to the main operating system.
-
Vendor Solutions: Some vendors offer versions of their software specifically designed to run without admin rights, albeit with reduced functionality.
If administrator privileges are not granted, you might encounter error messages or certain features might be disabled. Always refer to the software’s documentation or vendor support to understand the specific requirements and limitations.
6. What Are the Alternatives to Granting Full Admin Rights?
When full administrator rights seem risky or unnecessary, consider these alternatives to balance functionality and security:
-
Principle of Least Privilege: Grant users only the minimum permissions needed to perform their tasks, limiting the potential damage from malware or user error.
-
User Account Control (UAC): Keep UAC enabled to prompt for administrative credentials when needed, providing a layer of control without permanently elevating privileges.
-
Compatibility Mode: Run older software in compatibility mode, which can sometimes reduce the need for admin rights by emulating an older operating system environment.
-
Virtualization: Use virtual machines to isolate potentially risky applications from the host system, limiting the impact of any security breaches.
-
Group Policy: Utilize Group Policy settings in Windows to grant specific permissions to users or groups, rather than providing full admin access.
-
Standard User Accounts: Encourage users to work from standard user accounts and only switch to an administrator account when necessary for specific tasks.
-
Application Control Software: Implement application control software to restrict which applications can run with elevated privileges, reducing the overall attack surface.
According to a report by the Center for Internet Security (CIS), implementing the principle of least privilege is one of the most effective methods for reducing the risk of malware infections and insider threats.
7. How Does User Account Control (UAC) Impact Software Permissions?
User Account Control (UAC) is a security feature in Windows that affects how software permissions are managed. Here’s how:
-
Prompting for Elevation: UAC prompts users for permission before allowing software to make changes that require administrative privileges, helping prevent unauthorized modifications.
-
Virtualization of Registry and Files: For applications that attempt to write to protected areas, UAC can virtualize these changes, redirecting them to a user-specific location instead of the system-wide area.
-
Standard User Mode: When a user logs in with an administrator account, UAC runs their applications in standard user mode by default, limiting their privileges until explicitly elevated.
-
Customizable Security Levels: UAC allows users to adjust the level of notification, balancing security with convenience. However, disabling UAC entirely is not recommended due to the increased security risk.
-
Impact on Software Compatibility: Some older applications not designed with UAC in mind may not function correctly and may require compatibility mode or administrative privileges.
-
Reduced Malware Impact: By limiting the privileges of running software, UAC reduces the potential damage that malware can inflict on a system.
UAC serves as a critical component in Windows security, helping to ensure that software operates with the appropriate level of permissions and that users are aware of any potentially risky actions.
8. What Steps to Take if C4/C6 Software Fails to Run Without Admin Rights?
If C4/C6 software fails to run without administrator rights, try these steps to troubleshoot and resolve the issue:
-
Check Software Documentation: Review the software’s documentation for specific requirements and recommendations for running without admin rights.
-
Run in Compatibility Mode:
- Right-click the software’s executable file.
- Select “Properties.”
- Go to the “Compatibility” tab.
- Check “Run this program in compatibility mode for” and select an older version of Windows.
- Click “Apply” and then “OK.”
-
Adjust Permissions Manually:
- Right-click the software’s installation folder.
- Select “Properties.”
- Go to the “Security” tab.
- Click “Edit” and grant the necessary permissions (e.g., read, write) to the user account.
- Click “Apply” and then “OK.”
-
Use the Application Compatibility Toolkit: Microsoft’s Application Compatibility Toolkit can help identify and resolve compatibility issues that may be causing the software to require admin rights.
-
Check Event Logs: Review the Windows Event Logs for error messages or warnings that may provide clues about why the software is failing to run.
-
Contact Vendor Support: Reach out to the software vendor’s support team for assistance and specific guidance on running the software without admin rights.
-
Consider Virtualization: Run the software in a virtual machine, which can isolate it from the host system and potentially reduce the need for elevated privileges.
By systematically addressing these potential issues, you may be able to get the C4/C6 software running without compromising system security.
9. How Can Virtualization Help Manage Software Permissions?
Virtualization offers a robust solution for managing software permissions, particularly when dealing with applications that require elevated privileges. Here’s how:
-
Isolation: Virtual machines (VMs) create isolated environments, separating applications from the host operating system. This prevents software within the VM from directly accessing or modifying the host system.
-
Controlled Environment: Each VM can be configured with specific user accounts and permissions, ensuring that software operates within a controlled environment.
-
Reduced Security Risks: By isolating applications in VMs, the risk of malware or poorly written software affecting the host system is significantly reduced.
-
Simplified Management: Virtualization platforms provide tools for managing and monitoring VMs, making it easier to control software permissions and configurations.
-
Compatibility: VMs can emulate different operating systems, allowing older software that may require admin rights to run without compromising the security of the host system.
-
Snapshots and Backups: VMs can be easily backed up or snapshotted, allowing for quick restoration in case of issues or security breaches.
Popular virtualization solutions include VMware, VirtualBox, and Hyper-V, each offering features to enhance software permission management and overall system security.
10. Best Practices for Maintaining Security While Using Diagnostic Tools
To maintain robust security while using diagnostic tools like C4/C6, implement these best practices:
-
Use a Dedicated Computer: Dedicate a specific computer solely for diagnostic tasks to minimize exposure to other potential threats.
-
Keep Software Updated: Regularly update the diagnostic software, operating system, and antivirus software to patch vulnerabilities.
-
Strong Passwords: Use strong, unique passwords for all accounts, including the administrator account.
-
Firewall Protection: Ensure that the computer has a firewall enabled to block unauthorized network access.
-
Limited Network Connectivity: Only connect the computer to the internet or local network when necessary for updates or data transfer, reducing the attack surface.
-
Principle of Least Privilege: Operate the diagnostic software with the least privileges necessary, avoiding the use of an administrator account whenever possible.
-
Regular Backups: Perform regular backups of the computer’s data and system configurations to allow for quick recovery in case of a security breach or system failure.
-
Physical Security: Secure the computer physically to prevent unauthorized access or theft.
-
User Training: Provide training to users on security best practices, including how to recognize and avoid phishing attempts and other social engineering tactics.
-
Endpoint Detection and Response (EDR): Consider using an EDR solution to monitor the computer for suspicious activity and respond to potential threats in real-time.
By following these best practices, you can significantly enhance the security posture of your diagnostic environment and protect against potential cyber threats. The National Institute of Standards and Technology (NIST) provides comprehensive guidelines on cybersecurity best practices that can further enhance your security measures.
11. Understanding Software Compatibility and Operating Systems
Software compatibility is crucial for ensuring diagnostic tools function correctly within your operating system. Here’s what you need to know:
-
Operating System Requirements: Diagnostic software is often designed for specific operating systems (e.g., Windows 7, Windows 10, Windows 11). Always check the software’s documentation for compatibility.
-
32-bit vs. 64-bit: Ensure the software is compatible with your system’s architecture. 32-bit software can run on 64-bit systems, but 64-bit software requires a 64-bit operating system.
-
Driver Compatibility: Drivers for diagnostic interfaces must be compatible with the operating system. Incorrect or outdated drivers can lead to communication issues.
-
Virtual Machines: If the software is incompatible with your current OS, consider using a virtual machine with a compatible operating system.
-
Compatibility Mode: Windows offers compatibility mode, which allows older software to run by emulating an older operating system environment.
-
Software Updates: Keep your operating system and diagnostic software updated to ensure compatibility and security.
-
Testing: Before deploying diagnostic tools in a production environment, thoroughly test them in a controlled environment to identify and resolve any compatibility issues.
Addressing compatibility issues can prevent errors, improve performance, and ensure the longevity of your diagnostic equipment.
12. How Access Controls Affect Software Usage
Access controls play a vital role in determining how software is used and by whom. Here’s how they impact software usage:
-
User Permissions: Access controls define what actions a user can perform within the software, such as reading data, modifying settings, or executing specific functions.
-
Role-Based Access Control (RBAC): RBAC assigns permissions based on a user’s role within an organization, ensuring that each user has only the necessary access.
-
Principle of Least Privilege: This principle dictates that users should be granted only the minimum level of access required to perform their job duties, reducing the risk of misuse or accidental damage.
-
Authentication and Authorization: Access controls rely on authentication (verifying the user’s identity) and authorization (determining what the user is allowed to do).
-
Data Protection: By limiting access to sensitive data, access controls help protect against unauthorized disclosure or modification.
-
Audit Trails: Access control systems often include audit trails that track user activity, providing a record of who accessed what data and when.
-
Compliance: Implementing effective access controls helps organizations comply with regulatory requirements, such as GDPR and HIPAA.
Properly configured access controls not only enhance security but also improve operational efficiency by ensuring that users can access the tools and data they need without unnecessary restrictions.
13. The Importance of Regular Software Updates and Patches
Regular software updates and patches are essential for maintaining the security and functionality of diagnostic tools. Here’s why:
-
Security Vulnerabilities: Updates often include patches that address newly discovered security vulnerabilities, protecting against potential cyber attacks.
-
Bug Fixes: Updates fix bugs and other issues that can cause software to crash or malfunction, improving overall stability.
-
Compatibility: Updates ensure compatibility with the latest operating systems, drivers, and other software components.
-
New Features: Updates may introduce new features and enhancements that improve the user experience and expand the capabilities of the diagnostic tool.
-
Performance Improvements: Updates can optimize software performance, making it faster and more efficient.
-
Compliance: Keeping software updated helps organizations comply with regulatory requirements and industry best practices.
-
Vendor Support: Vendors typically provide ongoing support only for the latest versions of their software, so staying updated ensures access to timely assistance.
Failing to apply software updates and patches can leave systems vulnerable to attack, lead to operational issues, and limit access to the latest features and improvements. According to a study by IBM, over 60% of data breaches involve unpatched vulnerabilities.
14. Troubleshooting Common Installation Issues
When installing diagnostic software, you might encounter common issues. Here’s how to troubleshoot them:
-
Insufficient Permissions: Ensure you are running the installer with administrator privileges. Right-click the setup file and select “Run as administrator.”
-
Antivirus Interference: Temporarily disable your antivirus software during installation, but remember to re-enable it afterward.
-
Compatibility Issues: Run the installer in compatibility mode for an older version of Windows.
-
Missing Dependencies: Check if the software requires specific dependencies (e.g., .NET Framework, Visual C++ Redistributable) and install them if necessary.
-
Corrupted Installation Files: Download the installation files again from a trusted source to ensure they are not corrupted.
-
Driver Conflicts: Uninstall any conflicting drivers before installing the new ones. Use Device Manager to identify and resolve driver issues.
-
User Account Control (UAC): Adjust UAC settings to allow the installation to proceed without interruption.
-
Event Logs: Check the Windows Event Logs for error messages that may provide clues about the installation failure.
-
Vendor Support: Contact the software vendor’s support team for assistance with specific installation issues.
By systematically troubleshooting these potential problems, you can often resolve common installation issues and get your diagnostic software up and running smoothly.
15. Security Audits and Compliance in Automotive Diagnostics
Security audits and compliance are increasingly important in automotive diagnostics to protect sensitive data and ensure regulatory adherence. Here’s what you need to know:
-
Data Protection: Diagnostic tools often access and store sensitive vehicle and customer data, making data protection a primary concern.
-
Compliance Requirements: Automotive businesses must comply with various regulations, such as GDPR, CCPA, and industry-specific standards like ISO 27001.
-
Security Audits: Regular security audits can help identify vulnerabilities in diagnostic systems and processes, ensuring that security measures are effective.
-
Access Controls: Implementing strong access controls limits who can access diagnostic data and perform critical functions.
-
Data Encryption: Encrypting diagnostic data both in transit and at rest protects against unauthorized access.
-
Incident Response Plan: Having a well-defined incident response plan enables quick and effective action in the event of a security breach.
-
Employee Training: Training employees on security best practices and compliance requirements is essential for maintaining a strong security posture.
-
Third-Party Risk Management: Assessing the security practices of third-party vendors and service providers is crucial for mitigating supply chain risks.
By prioritizing security audits and compliance, automotive businesses can protect their data, maintain customer trust, and avoid costly penalties.
16. How to Choose Secure and Reliable Diagnostic Software
Choosing secure and reliable diagnostic software involves careful evaluation of several factors. Consider these guidelines:
-
Reputation: Research the vendor’s reputation and track record in the industry. Look for reviews, testimonials, and case studies.
-
Security Features: Evaluate the software’s security features, such as data encryption, access controls, and multi-factor authentication.
-
Compliance: Ensure the software complies with relevant industry standards and regulations (e.g., GDPR, CCPA, ISO 27001).
-
Update Frequency: Check how often the vendor releases software updates and security patches. Regular updates indicate a commitment to security and reliability.
-
Support: Assess the quality of the vendor’s support services. Responsive and knowledgeable support is essential for resolving issues quickly.
-
Third-Party Audits: Look for software that has undergone independent security audits by reputable third-party firms.
-
Integration: Ensure the software integrates seamlessly with your existing systems and processes.
-
Trial Period: Take advantage of trial periods or demos to test the software in your environment before making a purchase.
-
Cost: Consider the total cost of ownership, including licensing fees, maintenance costs, and potential upgrade expenses.
By carefully evaluating these factors, you can choose diagnostic software that meets your needs while maintaining a high level of security and reliability.
17. The Future of Automotive Diagnostics and Security
The future of automotive diagnostics is intertwined with advancements in security technology. Here’s what to expect:
-
Over-the-Air (OTA) Updates: OTA updates will become more prevalent for both software and firmware, enabling quick and efficient patching of vulnerabilities.
-
AI and Machine Learning: AI-powered security solutions will be used to detect and respond to threats in real-time, improving threat detection and response times.
-
Blockchain: Blockchain technology may be used to secure diagnostic data and prevent tampering, ensuring data integrity.
-
Cloud-Based Diagnostics: Cloud-based diagnostic platforms will offer greater scalability and flexibility, but also require robust security measures to protect data in the cloud.
-
Cybersecurity Standards: New cybersecurity standards and regulations will emerge to address the evolving threat landscape in the automotive industry.
-
Vehicle Security Operations Centers (VSOCs): VSOCs will be established to monitor and manage the security of connected vehicles, providing proactive threat detection and response.
-
Enhanced Authentication: Biometric authentication and other advanced authentication methods will be used to secure access to diagnostic systems.
-
Collaboration: Greater collaboration between automotive manufacturers, security researchers, and government agencies will be essential for addressing cybersecurity challenges.
As automotive technology continues to evolve, a proactive and adaptive approach to security will be crucial for protecting vehicles and their data from cyber threats.
18. How to Get Support and Training for C4/C6 Software
Obtaining adequate support and training is essential for effectively using C4/C6 software. Here’s how to access these resources:
-
Vendor Support: Contact the software vendor’s support team for technical assistance, troubleshooting, and guidance on using the software.
-
Online Documentation: Consult the software’s online documentation, including user manuals, FAQs, and knowledge base articles.
-
Training Courses: Enroll in training courses offered by the vendor or authorized training providers. These courses can provide in-depth knowledge and hands-on experience with the software.
-
Webinars and Tutorials: Attend webinars and watch tutorials to learn about specific features and best practices for using the software.
-
User Forums: Participate in user forums and online communities to connect with other users, share knowledge, and ask questions.
-
Remote Support: Take advantage of remote support services, where a support technician can remotely access your computer to diagnose and resolve issues.
-
On-Site Training: Consider on-site training for personalized instruction and support tailored to your specific needs.
-
Certification Programs: Pursue certification programs to demonstrate your expertise in using the software.
By leveraging these support and training resources, you can enhance your skills and maximize the value of your C4/C6 software.
19. Key Takeaways for Managing Software Permissions
Managing software permissions effectively is critical for maintaining system security and operational efficiency. Here are the key takeaways:
-
Principle of Least Privilege: Always grant users and software only the minimum permissions necessary to perform their tasks.
-
User Account Control (UAC): Keep UAC enabled and configured appropriately to provide a layer of control over software permissions.
-
Regular Updates: Ensure that all software, including the operating system and diagnostic tools, is regularly updated with the latest security patches.
-
Compatibility Mode: Use compatibility mode when necessary to run older software without requiring elevated privileges.
-
Virtualization: Consider virtualization to isolate potentially risky applications from the host system.
-
Access Controls: Implement strong access controls to limit who can access sensitive data and perform critical functions.
-
Security Audits: Conduct regular security audits to identify and address vulnerabilities in your systems and processes.
-
Employee Training: Train employees on security best practices and the importance of managing software permissions.
-
Vendor Support: Choose software from reputable vendors who provide ongoing support and security updates.
By following these key takeaways, you can effectively manage software permissions and protect your systems from potential threats.
20. Optimizing Your Workflow With DTS-MONACO.EDU.VN
At DTS-MONACO.EDU.VN, we understand the intricacies of car coding and ECU programming. Our comprehensive resources and expert guidance are designed to optimize your workflow and enhance your proficiency with tools like DTS-Monaco.
-
Comprehensive Training Programs: We offer in-depth training programs tailored to various skill levels. Whether you’re a beginner or an experienced technician, our courses cover everything from basic diagnostics to advanced coding techniques.
-
Step-by-Step Guides: Our step-by-step guides provide clear instructions and practical examples, making it easier to understand and implement complex procedures.
-
Software Solutions: We provide reliable software solutions that streamline your diagnostic and coding processes, ensuring efficiency and accuracy.
-
Expert Support: Our team of experienced professionals is available to provide expert support and answer any questions you may have.
-
Latest Industry Insights: Stay up-to-date with the latest trends and developments in the automotive industry through our articles, webinars, and resources.
-
Community Forum: Connect with other technicians and share your experiences and insights in our community forum.
With DTS-MONACO.EDU.VN, you can unlock the full potential of your diagnostic tools and elevate your skills in car coding and ECU programming. We are located at 275 N Harrison St, Chandler, AZ 85225, United States. Contact us via Whatsapp at +1 (641) 206-8880 or visit our website at DTS-MONACO.EDU.VN to learn more.
 Automotive diagnostics setup with laptop and diagnostic tool
Automotive diagnostics setup with laptop and diagnostic tool
Using a laptop connected with an RJ45 cable to the WAN port of a wireless router for diagnostics.
 Power button on ASUS wireless router
Power button on ASUS wireless router
Close-up of the power button location on an ASUS wireless router ready to be turned on.
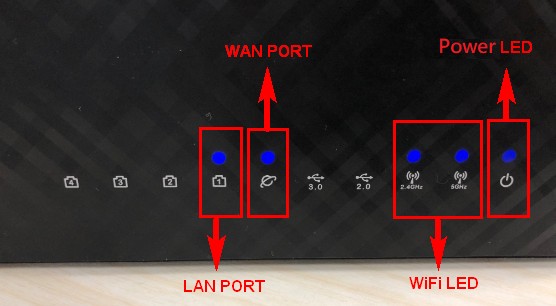 LED indicators on an ASUS router
LED indicators on an ASUS router
The LED indicators on the front of an ASUS wireless router showing power and network connectivity.
The login screen for the ASUS router web GUI, prompting for username and password to access settings.
 QIS setup page on ASUS router web GUI
QIS setup page on ASUS router web GUI
The Quick Internet Setup (QIS) page on the ASUS router web GUI for easy router configuration.
 Automatic IP setting on the WAN connection type page of an ASUS router
Automatic IP setting on the WAN connection type page of an ASUS router
Automatic IP settings on the WAN connection type page within an ASUS router’s web interface.
WAN DNS settings configuration on an ASUS router administration panel.
The DNS Privacy Protocol settings panel within an ASUS router configuration, allowing users to enhance their DNS privacy.
 Adding preset DNS servers in ASUS router settings
Adding preset DNS servers in ASUS router settings
Configuration interface showing how to add preset DNS servers within the ASUS router setup.
 Authentication settings under account settings in ASUS router web GUI
Authentication settings under account settings in ASUS router web GUI
Authentication settings located under account settings within the ASUS router’s web-based graphical user interface.
 Configuration panel for static IP settings on the WAN connection of an ASUS router
Configuration panel for static IP settings on the WAN connection of an ASUS router
Static IP settings in the WAN connection configuration panel of an ASUS router web interface.
 PPPoE WAN connection settings on an ASUS router configuration panel
PPPoE WAN connection settings on an ASUS router configuration panel
PPPoE settings configuration on the WAN connection panel of an ASUS router interface.
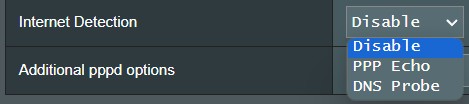 Internet detection settings on the web interface of an ASUS router showing the Disable option
Internet detection settings on the web interface of an ASUS router showing the Disable option
Internet detection settings on an ASUS router’s web interface, with “Disable” option highlighted.
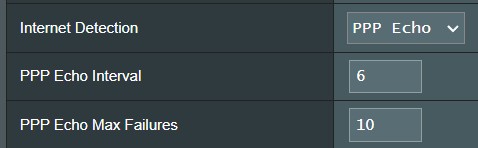 PPP Echo internet detection configuration on ASUS router panel
PPP Echo internet detection configuration on ASUS router panel
PPP Echo internet detection configuration on an ASUS router control panel.
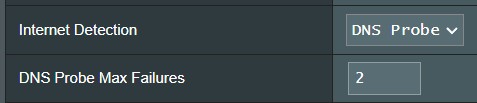 DNS Probe configuration for internet detection on an ASUS router panel
DNS Probe configuration for internet detection on an ASUS router panel
DNS Probe settings panel used for configuring internet detection on an ASUS router.
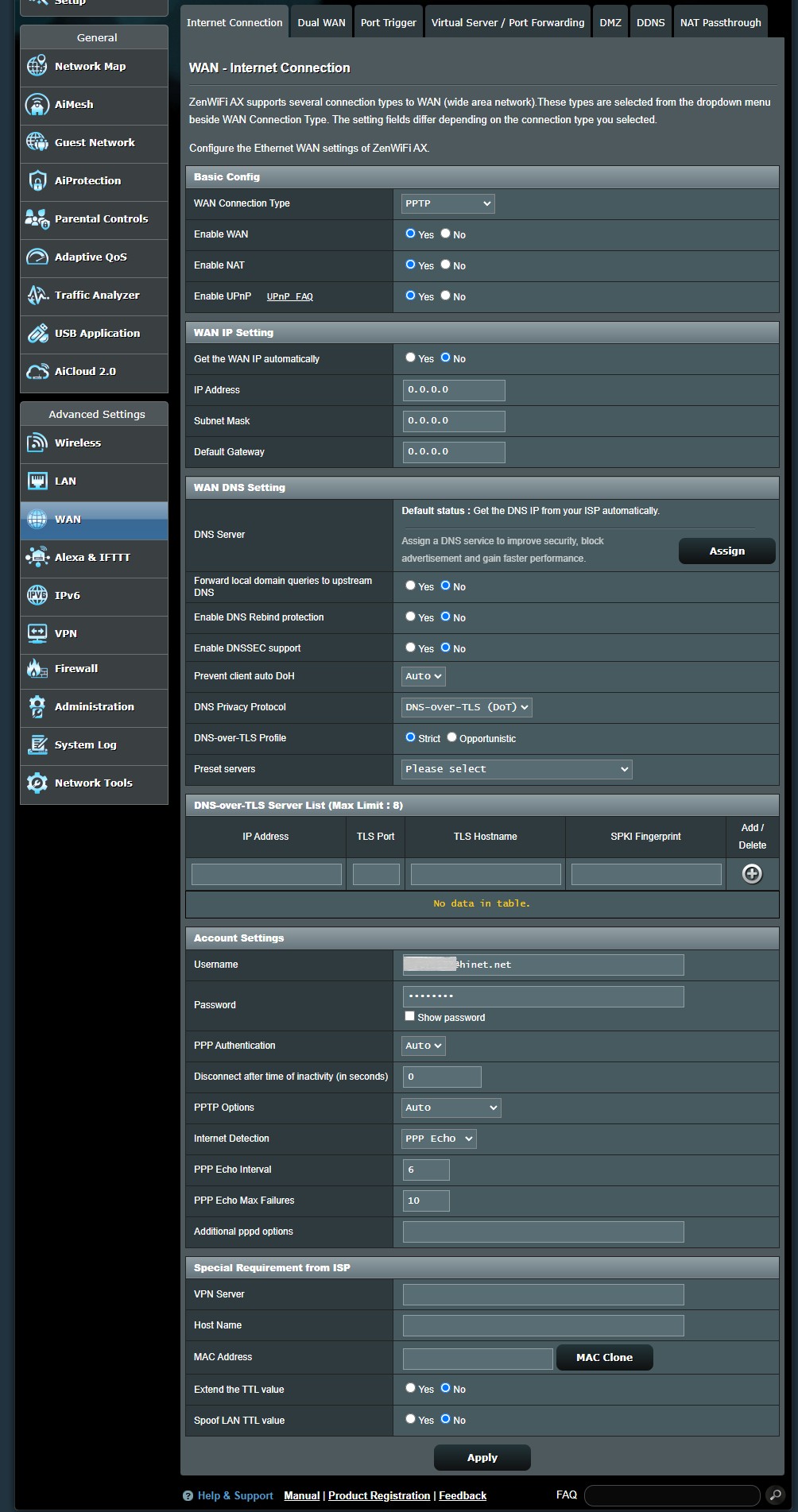 PPTP WAN connection settings on the ASUS router configuration page
PPTP WAN connection settings on the ASUS router configuration page
Configuration interface displaying PPTP settings for the WAN connection on an ASUS router.
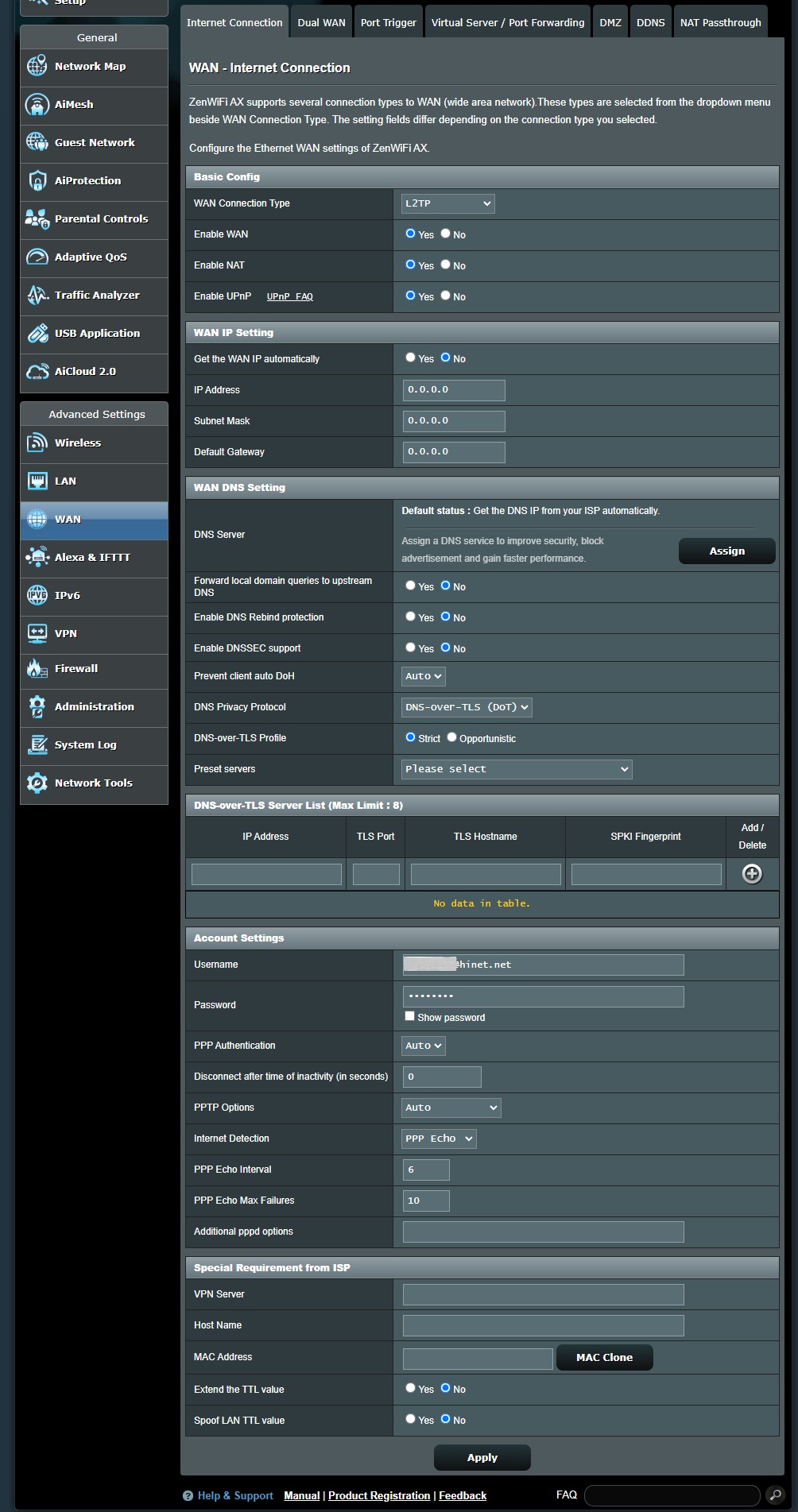 L2TP settings configuration on the ASUS router
L2TP settings configuration on the ASUS router
L2TP settings configuration panel as shown in the ASUS router’s administrative interface.
FAQ
Does DTS-Monaco require administrator privileges during installation?
Yes, DTS-MONACO typically requires administrator privileges during installation to properly configure system settings and install necessary drivers.
Why does diagnostic software need administrator rights?
Diagnostic software often needs administrator rights to make system-level changes, install drivers, and access protected system files required for proper functionality.
Is it safe to always run software with admin privileges?
No, it’s not generally safe. Running software with admin privileges increases the risk of malware exploitation and unauthorized access to sensitive data.
Can I run C4/C6 software without admin rights?
Some basic functions might work without admin rights, but features like ECU flashing and module programming usually require elevated privileges.