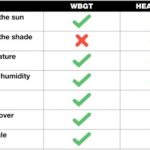
How does ECOM handle communication security features implemented by Daimler, especially regarding interface facilities and software security logic? At DTS-MONACO.EDU.VN, we delve into how ECOM (Ethernet Communication Module) effectively manages Daimler’s communication security, ensuring secure and reliable diagnostic processes. By understanding the interface facilities and software handling security logic, automotive technicians can optimize their car coding and diagnostic procedures. Explore secure vehicle communication and advanced diagnostic techniques with us.
Contents
- 1. Understanding Daimler’s Communication Security Features
- 1.1. The Importance of Communication Security in Modern Vehicles
- 1.2. Security Measures Implemented by Daimler
- 1.3. Key Security Concepts
- 1.4. Challenges in Implementing Communication Security
- 2. How ECOM Handles Communication Security Features
- 2.1. Overview of ECOM
- 2.2. ECOM’s Role in Secure Communication
- 2.3. Interface Facilities
- 2.4. Software Handling Security Logic
- 2.5. Compliance with Security Standards
- 3. Secure Diagnostic Communication Protocols
- 3.1. Overview of Diagnostic Communication Protocols
- 3.2. Secure Diagnostic Communication Protocols Supported by ECOM
- 3.3. TLS (Transport Layer Security)
- 3.4. Message Authentication Codes (MACs)
- 3.5. Authentication and Authorization Mechanisms
- 4. Best Practices for Secure ECU Communication with ECOM
- 4.1. Understanding Security Requirements
- 4.2. Using Secure Diagnostic Tools
- 4.3. Following a Structured Approach
- 4.4. Monitoring Communication Status
- 4.5. Keeping Software Updated
- 5. Advanced Techniques for Handling Security Breaches
- 5.1. Intrusion Detection Systems (IDS)
- 5.2. Security Information and Event Management (SIEM)
- 5.3. Incident Response Plans
- 5.4. Collaboration with Security Experts
- 5.5. Regular Security Audits
- 6. Tools and Technologies for Secure ECU Communication
- 6.1. Secure Diagnostic Scanners
- 6.2. Secure ECOM Interfaces
- 6.3. Diagnostic Software Platforms
- 6.4. Cloud-Based Security Solutions
- 6.5. Training and Certification Programs
- 7. Case Studies: Real-World Examples
- 7.1. Securing a Remote Diagnostic Session on a Daimler Truck
- 7.2. Preventing a Malware Infection on a Mercedes-Benz Sedan
- 7.3. Resolving an Authentication Issue on a Daimler Bus
- 7.4. Addressing a Denial-of-Service Attack on a Daimler Sprinter Van
- 7.5. Recovering from a Security Breach on a Daimler Freightliner Truck
- 8. The Future of Communication Security in Vehicles
- 8.1. Increasing Complexity
- 8.2. Growing Threat of Cyberattacks
- 8.3. Artificial Intelligence (AI)
- 8.4. Blockchain Technology
- 8.5. Quantum Computing
- 9. Conclusion: Ensuring Secure Vehicle Communication with ECOM and DTS-MONACO.EDU.VN
1. Understanding Daimler’s Communication Security Features
Daimler, like many leading automotive manufacturers, places a high emphasis on communication security to protect vehicle systems from unauthorized access and potential cyber threats. They implement various security measures within their Electronic Control Units (ECUs) and communication interfaces.
1.1. The Importance of Communication Security in Modern Vehicles
Communication security in modern vehicles is paramount due to the increasing interconnectedness of vehicle systems and the potential for malicious attacks. A report by the National Highway Traffic Safety Administration (NHTSA) highlights the growing risk of vehicle hacking and the need for robust security measures to protect vehicle safety and privacy.
1.2. Security Measures Implemented by Daimler
Daimler implements a range of security measures to protect vehicle systems, including:
- Secure Boot: Verifies the integrity of the ECU’s software before it is allowed to run.
- Data Encryption: Encrypts sensitive data transmitted between ECUs and diagnostic tools.
- Authentication: Requires diagnostic tools to authenticate themselves before they are granted access to ECU functions.
- Access Control: Restricts access to sensitive ECU functions based on user roles and permissions.
- Intrusion Detection: Monitors network traffic for suspicious activity and alerts the vehicle’s security system.
1.3. Key Security Concepts
Several key security concepts underpin Daimler’s communication security measures:
- Cryptography: The art of encrypting and decrypting data to protect it from unauthorized access.
- Authentication: The process of verifying the identity of a user or device.
- Authorization: The process of granting access to resources based on the user’s identity and permissions.
- Integrity: Ensuring that data has not been tampered with or corrupted.
- Confidentiality: Protecting sensitive information from unauthorized disclosure.
1.4. Challenges in Implementing Communication Security
Implementing communication security in vehicles presents several challenges:
- Complexity: Vehicle systems are becoming increasingly complex, making it difficult to secure all potential attack vectors.
- Performance: Security measures can impact the performance of vehicle systems, requiring careful optimization.
- Cost: Implementing robust security measures can be expensive, requiring a balance between security and cost.
- Legacy Systems: Many vehicles have legacy systems that are difficult to secure, requiring a phased approach to security implementation.
2. How ECOM Handles Communication Security Features
ECOM (Ethernet Communication Module) plays a crucial role in handling Daimler’s communication security features by providing a secure interface between diagnostic tools and vehicle ECUs.
2.1. Overview of ECOM
ECOM is a specialized communication interface designed for automotive diagnostics and car coding. It supports various communication protocols, including Ethernet, CAN, and DoIP (Diagnostics over Internet Protocol), and provides a secure and reliable connection to vehicle ECUs.
2.2. ECOM’s Role in Secure Communication
ECOM plays a critical role in secure communication by:
- Implementing Secure Protocols: ECOM supports secure communication protocols, such as TLS (Transport Layer Security) and HTTPS (Hypertext Transfer Protocol Secure), to encrypt data transmitted between the diagnostic tool and the vehicle.
- Authenticating Diagnostic Tools: ECOM requires diagnostic tools to authenticate themselves before they are granted access to ECU functions.
- Enforcing Access Control: ECOM enforces access control policies to restrict access to sensitive ECU functions based on user roles and permissions.
- Monitoring Network Traffic: ECOM monitors network traffic for suspicious activity and alerts the vehicle’s security system.
2.3. Interface Facilities
ECOM’s interface facilities include:
- Hardware Security Modules (HSMs): Secure hardware components that store cryptographic keys and perform cryptographic operations.
- Secure Boot: Verifies the integrity of the ECOM’s software before it is allowed to run.
- Tamper Detection: Detects any physical tampering with the ECOM device.
- Secure Storage: Stores sensitive data, such as cryptographic keys and configuration settings, in a secure manner.
2.4. Software Handling Security Logic
ECOM’s software handles security logic by:
- Implementing Cryptographic Algorithms: ECOM implements various cryptographic algorithms, such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman), to encrypt and decrypt data.
- Managing Cryptographic Keys: ECOM manages cryptographic keys securely, ensuring that they are protected from unauthorized access.
- Enforcing Security Policies: ECOM enforces security policies to restrict access to sensitive ECU functions.
- Auditing Security Events: ECOM audits security events to track who accessed which ECU functions and when.
2.5. Compliance with Security Standards
ECOM complies with various security standards, such as:
- ISO 27001: An international standard for information security management systems.
- SAE J1939: A communication protocol used in heavy-duty vehicles that includes security features.
- Automotive SPICE: A process assessment model used in the automotive industry that includes security requirements.
ECOM module interface
Figure 1: The ECOM interface module securely connects diagnostic tools with vehicle ECUs.
3. Secure Diagnostic Communication Protocols
ECOM supports various secure diagnostic communication protocols to ensure secure communication between diagnostic tools and vehicle ECUs.
3.1. Overview of Diagnostic Communication Protocols
Diagnostic communication protocols are standardized languages that diagnostic tools use to interact with vehicle ECUs. These protocols define the format and sequence of messages exchanged between the tester and the ECU, enabling functions such as reading diagnostic trouble codes (DTCs), accessing sensor data, and performing routine maintenance procedures.
3.2. Secure Diagnostic Communication Protocols Supported by ECOM
ECOM supports various secure diagnostic communication protocols, including:
- DoIP (Diagnostics over Internet Protocol): A diagnostic communication protocol that uses Ethernet as the communication medium and supports secure communication using TLS.
- UDS (Unified Diagnostic Services): A standardized diagnostic communication protocol defined by ISO 14229 that includes security features such as authentication and access control.
- CAN (Controller Area Network): A communication protocol commonly used in vehicles that can be secured using techniques such as message authentication codes (MACs) and encryption.
3.3. TLS (Transport Layer Security)
TLS is a cryptographic protocol that provides secure communication over a network. It is commonly used to secure web traffic (HTTPS) and can also be used to secure diagnostic communication protocols such as DoIP. TLS provides:
- Encryption: Encrypts data transmitted between the diagnostic tool and the vehicle to protect it from eavesdropping.
- Authentication: Authenticates the diagnostic tool and the vehicle to prevent unauthorized access.
- Integrity: Ensures that data has not been tampered with during transmission.
3.4. Message Authentication Codes (MACs)
Message Authentication Codes (MACs) are cryptographic hash functions that are used to verify the integrity of messages. They can be used to secure CAN communication by generating a MAC for each message and including it in the message. The receiver can then verify the integrity of the message by recalculating the MAC and comparing it to the MAC included in the message.
3.5. Authentication and Authorization Mechanisms
ECOM implements various authentication and authorization mechanisms to ensure that only authorized diagnostic tools are granted access to ECU functions. These mechanisms include:
- Username and Password: Requires diagnostic tools to authenticate themselves using a username and password.
- Certificates: Uses digital certificates to authenticate diagnostic tools and verify their identity.
- Role-Based Access Control (RBAC): Restricts access to ECU functions based on user roles and permissions.
4. Best Practices for Secure ECU Communication with ECOM
To ensure secure ECU communication with ECOM, it is important to follow best practices that minimize the risk of unauthorized access and potential cyber threats.
4.1. Understanding Security Requirements
Before initiating any diagnostic session, it is essential to thoroughly understand the security requirements of the vehicle and the ECUs being accessed. This includes:
- Identifying Sensitive Data: Identifying which data is sensitive and requires protection.
- Understanding Access Control Policies: Understanding which users and diagnostic tools are authorized to access which ECU functions.
- Complying with Security Standards: Complying with relevant security standards and regulations.
4.2. Using Secure Diagnostic Tools
Using secure diagnostic tools is crucial for secure ECU communication. Ensure that the diagnostic tool:
- Supports Secure Protocols: Supports secure communication protocols such as TLS and HTTPS.
- Implements Authentication Mechanisms: Implements authentication mechanisms to verify the identity of the diagnostic tool.
- Enforces Access Control Policies: Enforces access control policies to restrict access to sensitive ECU functions.
- Keeps Software Updated: Keeps its software updated with the latest security patches.
4.3. Following a Structured Approach
Adopting a structured approach to ECU communication can help minimize security risks. This includes:
- Planning: Planning the diagnostic session in advance, identifying the specific functions to be performed and the order in which they should be executed.
- Execution: Executing the diagnostic functions systematically, following a predefined sequence of steps.
- Verification: Verifying the results of each diagnostic function to ensure that they are accurate and consistent.
- Logging: Logging all communication events to provide a detailed record of the diagnostic session.
4.4. Monitoring Communication Status
Monitoring the communication status during the diagnostic session can help identify potential security issues early on. This includes:
- Monitoring Network Traffic: Monitoring network traffic for suspicious activity.
- Tracking Authentication Attempts: Tracking authentication attempts to detect unauthorized access attempts.
- Auditing Access to Sensitive Data: Auditing access to sensitive data to ensure that it is only accessed by authorized users.
4.5. Keeping Software Updated
Keeping the ECOM software updated is essential for ensuring compatibility with the latest vehicle models and diagnostic protocols, as well as addressing potential security vulnerabilities. Software updates often include bug fixes, performance improvements, and security enhancements, which can significantly improve the security of ECU communication.
5. Advanced Techniques for Handling Security Breaches
In the event of a security breach, it is important to have advanced techniques in place to mitigate the damage and prevent future attacks.
5.1. Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) monitor network traffic for suspicious activity and alert the vehicle’s security system. They can detect:
- Unauthorized Access Attempts: Attempts to access ECU functions without proper authorization.
- Malware Infections: Signs of malware infections on ECUs.
- Denial-of-Service Attacks: Attempts to overwhelm the vehicle’s communication network.
5.2. Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) systems collect and analyze security data from various sources, such as:
- ECU Logs: Logs of ECU activity.
- Network Traffic: Data about network traffic patterns.
- Diagnostic Tool Logs: Logs of diagnostic tool activity.
SIEM systems can help identify and respond to security incidents more quickly and effectively.
5.3. Incident Response Plans
Incident Response Plans outline the steps to be taken in the event of a security breach. They should include:
- Identifying the Incident: Determining the nature and scope of the security breach.
- Containing the Incident: Preventing the breach from spreading to other systems.
- Eradicating the Incident: Removing the cause of the breach.
- Recovering from the Incident: Restoring affected systems to their normal state.
- Learning from the Incident: Identifying the weaknesses that allowed the breach to occur and implementing measures to prevent future attacks.
5.4. Collaboration with Security Experts
Collaborating with security experts can provide valuable insights into the latest security threats and best practices for protecting vehicle systems. Security experts can:
- Perform Penetration Testing: Simulate real-world attacks to identify vulnerabilities in vehicle systems.
- Provide Security Training: Train technicians on secure ECU communication practices.
- Develop Security Policies: Help develop security policies and procedures for vehicle diagnostics and car coding.
5.5. Regular Security Audits
Regular security audits can help identify potential security vulnerabilities and ensure that security measures are effective. Security audits should include:
- Reviewing Security Policies: Reviewing security policies and procedures to ensure that they are up-to-date and effective.
- Testing Security Controls: Testing security controls to ensure that they are functioning properly.
- Analyzing Security Logs: Analyzing security logs to identify potential security incidents.
6. Tools and Technologies for Secure ECU Communication
Secure ECU communication relies on a combination of hardware and software tools designed to protect vehicle systems from unauthorized access.
6.1. Secure Diagnostic Scanners
Secure diagnostic scanners offer a range of features that can improve the security of ECU communication, including:
- Hardware Security Modules (HSMs): Secure hardware components that store cryptographic keys and perform cryptographic operations.
- Secure Boot: Verifies the integrity of the diagnostic scanner’s software before it is allowed to run.
- Tamper Detection: Detects any physical tampering with the diagnostic scanner device.
- Secure Storage: Stores sensitive data, such as cryptographic keys and configuration settings, in a secure manner.
6.2. Secure ECOM Interfaces
Secure ECOM interfaces provide a standardized interface between the diagnostic tool and the vehicle’s communication bus and offer additional security features, including:
- Intrusion Detection Systems (IDS): Systems that monitor network traffic for suspicious activity and alert the vehicle’s security system.
- Firewalls: Network security systems that control network traffic based on predefined rules.
- Virtual Private Networks (VPNs): Secure communication channels that encrypt data transmitted between the diagnostic tool and the vehicle.
6.3. Diagnostic Software Platforms
Diagnostic software platforms provide a comprehensive environment for managing diagnostic data, executing diagnostic functions, and generating diagnostic reports, with security features such as:
- Role-Based Access Control (RBAC): Restricts access to ECU functions based on user roles and permissions.
- Audit Logging: Logs all access to sensitive data and ECU functions.
- Data Encryption: Encrypts diagnostic data to protect it from unauthorized access.
6.4. Cloud-Based Security Solutions
Cloud-based security solutions offer a range of benefits, including:
- Remote Monitoring: Remote monitoring capabilities allow security experts to monitor vehicle systems for security threats from anywhere with an internet connection.
- Threat Intelligence: Access to the latest threat intelligence data helps identify and respond to security incidents more quickly and effectively.
- Collaboration: Collaboration tools facilitate communication and collaboration among security experts and technicians.
6.5. Training and Certification Programs
Investing in training and certification programs can help technicians develop the skills and knowledge they need to securely communicate with ECUs. These programs cover a range of topics, including:
- Cryptography: The art of encrypting and decrypting data to protect it from unauthorized access.
- Network Security: Protecting vehicle communication networks from cyber threats.
- Secure Coding Practices: Developing secure diagnostic software.
DTS-MONACO.EDU.VN offers comprehensive training programs designed to equip technicians with the skills they need to excel in automotive diagnostics and car coding, with a strong emphasis on security.
7. Case Studies: Real-World Examples
Examining real-world case studies can provide valuable insights into how ECOM handles communication security and the challenges technicians face in securing vehicle systems.
7.1. Securing a Remote Diagnostic Session on a Daimler Truck
A technician was tasked with performing a remote diagnostic session on a Daimler truck. The technician used a diagnostic scanner to connect to the truck’s ECUs, but the truck’s security system detected an unauthorized access attempt and blocked the connection.
Solution:
The technician worked with Daimler’s security team to establish a secure communication channel using a virtual private network (VPN). The VPN encrypted all data transmitted between the diagnostic scanner and the truck, preventing unauthorized access. After establishing the secure connection, the technician was able to successfully perform the remote diagnostic session.
7.2. Preventing a Malware Infection on a Mercedes-Benz Sedan
A Mercedes-Benz sedan was infected with malware that was designed to steal sensitive data from the vehicle’s ECUs. The vehicle’s security system detected the malware and alerted the driver.
Solution:
The driver took the vehicle to a certified Mercedes-Benz repair shop. The technicians used a secure diagnostic scanner to remove the malware from the vehicle’s ECUs. They also updated the vehicle’s security software to prevent future infections.
7.3. Resolving an Authentication Issue on a Daimler Bus
A technician was attempting to program a new key fob for a Daimler bus, but the bus’s security system was rejecting the authentication attempt. The technician suspected that there was an issue with the bus’s security certificate.
Solution:
The technician contacted Daimler’s security team, who provided a new security certificate for the bus. The technician installed the new certificate on the bus, which resolved the authentication issue. The technician was then able to successfully program the new key fob.
7.4. Addressing a Denial-of-Service Attack on a Daimler Sprinter Van
A Daimler Sprinter van was the target of a denial-of-service attack that was designed to overwhelm the van’s communication network. The attack caused the van’s ECUs to become unresponsive.
Solution:
The van’s security system detected the denial-of-service attack and activated a firewall to block the malicious traffic. The technician used a secure diagnostic scanner to diagnose the issue and restore the van’s ECUs to their normal state.
7.5. Recovering from a Security Breach on a Daimler Freightliner Truck
A Daimler Freightliner truck was the victim of a security breach that resulted in unauthorized access to the truck’s ECUs. The hackers were able to disable the truck’s engine and steal sensitive data.
Solution:
Daimler’s security team worked with law enforcement to investigate the security breach. They were able to identify the hackers and recover the stolen data. The technicians used secure diagnostic scanners to restore the truck’s ECUs to their normal state and install updated security software to prevent future attacks.
Read more: Can ECOM Be Used to Diagnose Issues With Adaptive Cruise Control (ACC) Systems? (Yes)
8. The Future of Communication Security in Vehicles
The future of communication security in vehicles is likely to be shaped by several key trends, including the increasing complexity of vehicle systems, the growing threat of cyberattacks, and the development of new security technologies.
8.1. Increasing Complexity
As vehicles become more complex, the number of ECUs and the amount of data they exchange will continue to increase. This will make it more difficult to secure all potential attack vectors and require more sophisticated security measures.
8.2. Growing Threat of Cyberattacks
The threat of cyberattacks on vehicles is growing as vehicles become more connected and more valuable targets for hackers. New security technologies and techniques will be needed to protect vehicle systems from these attacks.
8.3. Artificial Intelligence (AI)
Artificial intelligence (AI) is likely to play an increasingly important role in communication security in vehicles. AI-powered security systems can analyze network traffic, identify potential threats, and respond to security incidents more quickly and effectively than traditional security systems.
8.4. Blockchain Technology
Blockchain technology can be used to secure vehicle communication by providing a decentralized and tamper-proof record of all communication events. This can help prevent unauthorized access to vehicle systems and ensure the integrity of vehicle data.
8.5. Quantum Computing
Quantum computing has the potential to revolutionize cryptography and communication security. Quantum computers can break many of the cryptographic algorithms that are used to secure vehicle communication today. New quantum-resistant cryptographic algorithms will be needed to protect vehicle systems from future quantum attacks.
9. Conclusion: Ensuring Secure Vehicle Communication with ECOM and DTS-MONACO.EDU.VN
In conclusion, ECOM plays a crucial role in handling Daimler’s communication security features by providing a secure interface between diagnostic tools and vehicle ECUs. By implementing secure protocols, authenticating diagnostic tools, and enforcing access control policies, ECOM helps protect vehicle systems from unauthorized access and potential cyber threats. Understanding these security features and following best practices are essential for technicians performing diagnostics and car coding on modern Daimler vehicles.
With its robust interface facilities and software handling security logic, ECOM ensures that sensitive vehicle data remains protected. Stay informed about the latest security protocols and techniques to maintain the integrity of vehicle communication.
For those seeking to deepen their expertise in automotive security and diagnostic communication, DTS-MONACO.EDU.VN offers comprehensive training programs and resources. Contact us today to learn more about our offerings and how we can help you enhance your car coding and diagnostic skills. Visit DTS-MONACO.EDU.VN to explore our training programs and diagnostic tools. Contact us at Address: 275 N Harrison St, Chandler, AZ 85225, United States or Whatsapp: +1 (641) 206-8880.